MegaSack DRAW - This year's winner is user - rgwb
We will be in touch
Looks like they've taken the decision to shut down a large part of the NHS IT infrastructure to protect it from attack.
[url= https://www.theguardian.com/society/2017/may/12/hospitals-across-england-hit-by-large-scale-cyber-attack ]https://www.theguardian.com/society/2017/may/12/hospitals-across-england-hit-by-large-scale-cyber-attack[/url]
Try not to get sick for a few hours people 🙁
beggars belief sometimes... what are the hackers trying to prove. !?^"%£^**
tuskaloosa - Member
beggars belief sometimes... what are the hackers trying to prove. !?^"%£^**
Nothing, it's just the usual ransomware by the sound of it. Bloody annoying but it is fairly indiscriminate when it comes to targets. Some of it is very advanced in terms of avoiding detection as well.
I hear from (cough) facebook GP groups (/cough) that some GP software servers are down too.
Not mine however. Singletrackworld and the Poke are what leads to naff productivity at my end...
DrP
Yep all our systems have gone down
Just hope contingency allows clinical things to keep going. Major incident plans in action
Attack a bank etc is one thing, this could affect people's lives 🙁
bits of Blackpool and Blackburn effected AFAIK
Should have used Linux.
Ugh. I work in the IT dept of a local authority.
We had exactly the same last year. It was a massive pain in the arse, ended up using a similar strategy to that which it looks like they're using. Minimise attack surface, repair, slowly bring stuff back up in conjunction with AV supplier. Painful enough for a small authority, going to be hideous for the NHS 🙁
The attackers probably aren't targeting the NHS specifically, there'll just be a script that goes around probing ports and then seeing if it can install the ransomware. The other possibility is that it was on a memory stick and only became activated if it found it was on a large network or similar trigger.
BBC reporting:
[i]GPs are resorting to using pen and paper[/i]
read into that what you want.
GPs are resorting to using pen and paper
'Uh Oh! Your files have been encrypted. By indecipherable handwriting!
The other possibility is that it was on a memory stick and only became activated if it found it was on a large network or similar trigger.
The non joined-up nature of NHS IT is our greatest defence. 🙂
Kind of the hackers to offer payment terms for the poor!
The attackers probably aren't targeting the NHS specifically, there'll just be a script that goes around probing ports and then seeing if it can install the ransomware. The other possibility is that it was on a memory stick and only became activated if it found it was on a large network or similar trigger.
As you say, I'd be very, very surprised if it was targeted. It's 'just' run of the mill, indiscriminate malware 🙁
I know if one that came in via email, was blocked, and then subsequently released, upon which the recipient opened it. At which point it identified attack surface, which are usually open file shares on servers, hops on to them, and propagates from there.
I await the Russian conspiracy theorists though. (And to be fair it's almost certainly of Russian origin)
There was a really interesting RadioLab about this last year as well.
#nhsspendingonITendsinfailureshocker
Re: memory sticks. Read up on [url= https://www.wired.com/2014/11/countdown-to-zero-day-stuxnet/ ]Stuxnet[/url] which was the virus that attempted to destroy Iran's nuclear fuel enrichment program. Really, really targeted: it would only deploy if it found a particular version of certain firmware in a certain configuration. Basically they knew exactly what they were after. The above link is quite a long article but well worth reading.
We have also been targeted today by ransomware affected emails, not NHS, so this could be part of a much larger ransomware attack.
Affecting our local Dgh. No reporting on CT/xray/bloods. Handwritten triage and wristbands. It's distinctly possible that real patient harm will come from this attack due to the delays in diagnosis and treatment.
BBC reporting:[b]GPs are resorting to using pen and paper[/b]
read into that what you want.
...then sent on to Bletchley Park to be decoded! 😀
[i]#nhsspendingonITendsinfailureshocker[/i]
although for the most part they'll just be using commercial software the same as everyone else.
The issue with the NHS is that there's so much linked infrastructure that malware can propogate itself very quickly across a large number of sites.
It'll probably end up beign someone who brought a memory stick from home or went to dropbox to pick a file up.
Fixed.It'll probably end up being [strike]someone[/strike] a domain admin who brought a memory stick from home or went to dropbox to pick a file up.
Telefonica telling employees to disconnect 'puters from networks.
[url= https://teiss.co.uk/2017/05/12/telefonica-ransomware-attack-employees-asked-pull-plug-computers/ ]https://teiss.co.uk/2017/05/12/telefonica-ransomware-attack-employees-asked-pull-plug-computers/[/url]
The worst thing about all of this is that the banks could if they wished trace the route of the money.. but banking secrecy wins.
GP software servers
Is that some sort of slave labour that GPs can afford on their £1,000,000 p.a. salaries?
Does anybody actually pay to this sort of demand?
Yes.. in my experience.. lots do pay.
Does anybody actually pay to this sort of demand?
People with valuable data and no backups. It's the only way to get the data back. Think of it as an idiot tax.
The worst thing about all of this is that the banks could if they wished trace the route of the money.. but banking secrecy wins.
Bitcoins?
Yes. Everyone from private businesses to local authorities to private individuals have paid.
Is be very surprised if the money could be traced, as the ransom demand will almost certainly be payable only via bitcoin.
Edit: beaten to it!
I don't know much about cyber security, but presumably this software is constantly prowling the net looking for vulnerable ports or whatever, so you'd expect the problem to be much more widespread unless they were slack with thier firewalls etc?
I suppose it's more likely a user with too many account privelidges unwittingly caused it?
Think of it as an idiot tax.
Dressed like that they were asking for it
mattyfez - Member
I don't know much about cyber security, but presumably this software is constantly prowling the net looking for vulnerable ports or whatever, so you'd expect the problem to be much more widespread unless they were slack with thier firewalls etc?I suppose it's more likely a user with too many account privelidges unwittingly caused it?
It is very widespread, there are a huge number of variants and there are new ones released constantly targeting new exploits.
I have seen the devastation ransomwhere caused at a biotech company, it was not pretty. And they were pretty shit hot on computer security. Unfortunately they also found out that day that some of their backups had been silently failing.
Strong and Stable eh?
May got a pasting from NHS staff calling in on LBC this morning too, she's lucky it wasn't after this...
I think most ransomware comes from emails, not from hacking attacks. Humans are the weakest link in the security chain.
I know of two companies affected by this.
1 reverted back to previous nights backup. Lost half a days work.
The other paid up and got a decryption key. It worked.
In one of the instances the culprit was a macro enabled word document e-mailed in. Downloaded and executed code from the internet on opening. It then encrypted every file on any share that was connected.
I feel for the NHS on this one. Going to be very painful to recover...
You make it sound so sinister.this software is constantly prowling the net
MSP is correct. It (or they rather) just relies on the easiest attack vector. Dopey humans and their inbox. Someone runs the program they have been sent (cutest_kitten_EVER.jpg), and then it runs in the background encrypting any drives on your computer. Which in this case looks like someone with a high level of access to write to network shares.
.
Why aren't email clients sandboxed?
An email client needs to be able to [i]read[/i] files, and create [i]new[/i] files, but not [i]modify[/i] existing files. Along with any child processes.
Dressed like that they were asking for it
I didn't say they deserved it. Rather it's an eggs-and-baskets disaster waiting to happen.
Because it's not the email client executing the program. It's the user.
Which is why ransomware like this is hard to stop. People (and computers if we want to get technical) need to read, write and execute files to do their job.
Because it's not the email client executing the program. It's the user.
Quite. Sandbox emails - then what happens when a user gets an emailed spreadsheet, opens it, edits it and wants to save it to their Documents folder?
Which is why ransomware like this is hard to stop.
It's trivial to stop. Remove "execute" privileges from temp directories. You can do it organisation-wide via Group Policy in a few mouse clicks. (Ok, users can bypass this by saving the attachments elsewhere, but it'll stop most if not all double-click-oh-shit infections.)
Also effective but slightly more difficult: Remove rights to run unsigned code, and / or whitelist allowed apps for regular users.
I think this may be using a SMB vulnerability rather than just a standard easily stopped executable.
Meh - they have business continuity procedures, don’t they? Just use them. That’s what they are for.
Oh, they don’t you say? Well, somebody’s head should be on the block after this, then...
edit - for context, I used to work for a Pharma company, supplying the NHS. We were *required* to have business continuity procedures, and test them, before the NHS would even deal with us.
Rachel
It's still got to get in in the first place though.
Doesn't surprise me one bit, the NHS it utterly reliant on IT and largely refuses to invest money on it.
Doesn't surprise me one bit, the NHS it utterly reliant on IT and largely refuses to invest money on it.
Moreover, when they do invest it's not always wisely. I was once involved in a large NHS roll-out and it was clear from the outset that what they'd bought was never going to work / do what they wanted. Multi-million pound system, was still a cluster-youknowwhat when I'd stopped being involved and I believe it was scrapped in the end.
If you don't have a sprawling lashed up desktop environment that is still using Windows XP.It's trivial to stop
Group Policy still applies to XP, it is (IIRC) Windows 2000 technology.
Good background [url= https://www.scmagazineuk.com/hospitals-turn-patients-away-as-nhs-caught-up-in-global-ransomware-attack/article/658864/ ]here[/url]
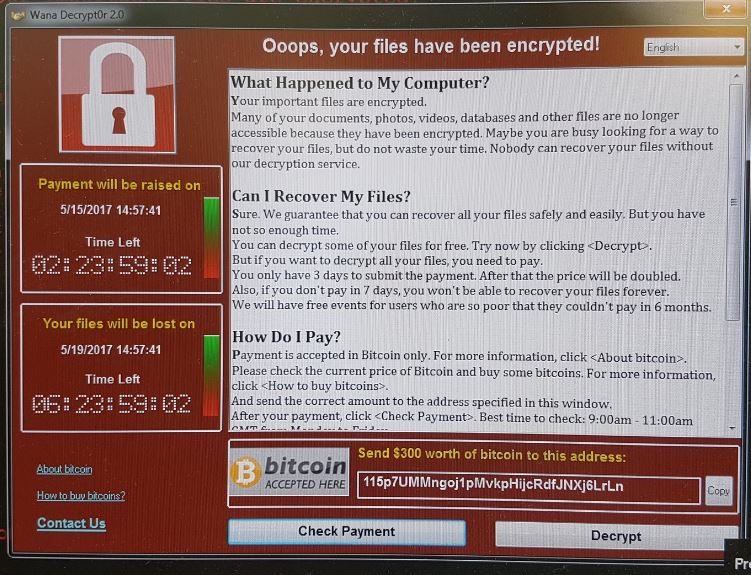
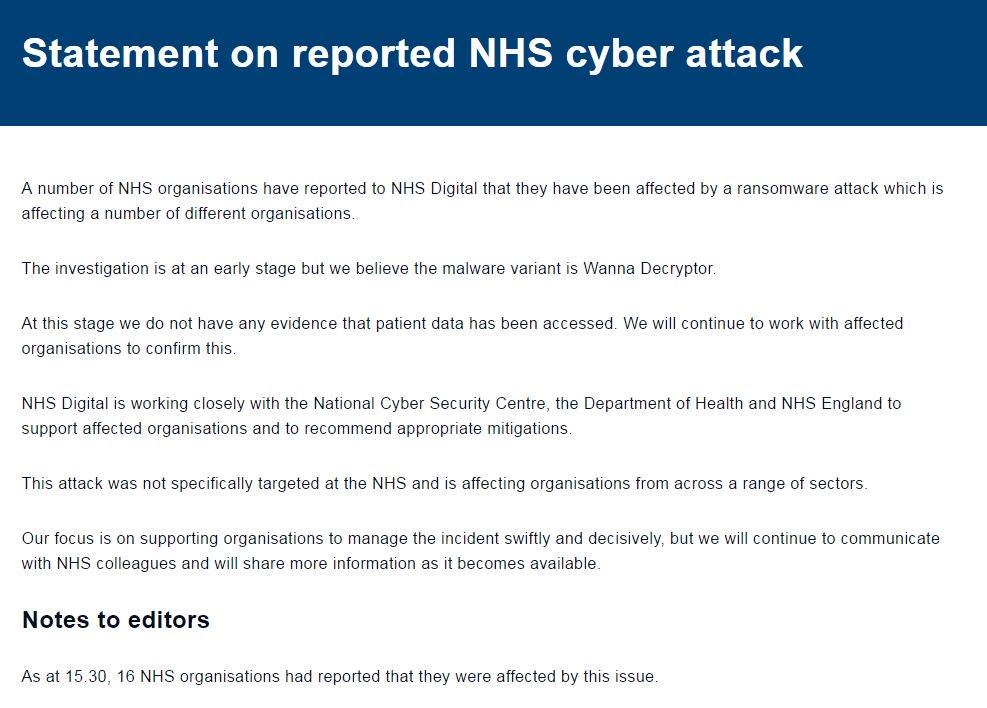
While WannaCryptor is a ransomware tool, the chaos caused by this incident comes from the fact that it is able to jump from computer to computer using EternalBlue/MS17-010/SMB, a vulnerability [b]developed by the NSA[/b] and released into the wild by Shadow Brokers.
Rachel the business continuity procedures involve cancelling all appointments. Staff not being able to contact each other. Thats not without consequences.
Had a double MRI today after a 4 week wait, hoping data isn't lost although I will not complain as its not life threatening to have to re-do them.
Ahh sounds about right, so the need to snoop on anyone and everyone to 'keep us safe from terrorist attacks' just Brought a national health system to its knees, potentialy causing many more deaths than any terrorist attack.
And now we also have the snoopers charter in the UK to worry about too.
Slow clap. Well done everyone. I'm sure I read one news story that one A&E was essentially telling people no to come as they were effectively shut down... If that's not costing life then I don't know what is.
I thought clapping had been banned!
vulnerability developed by the NSA and released into the wild by Shadow Brokers.
I think you mean exploit, not vulnerability. The vulnerability is in Windows SMB server and a patch was issued mid-March.
If it is that exploit, then it kind of explains things.
[i]In March, Microsoft patched the SMB Server vulnerability (MS17-010) exploited by ETERNALBLUE, and it's clear that some people have been slow to apply the critical update, are unable to do so, or possibly just don't care.
The fix is available for Windows Vista SP2, Windows 7, Windows 8.1, Windows RT 8.1, Windows 10, Windows Server 2008 SP2, Windows Server 2008 R2 SP1, Windows Server 2012 and Windows Server 2012 R2, Windows Server 2016, and Server Core. If you have an older vulnerable system, such as XP or Server 2003, you're out of luck[/i].
https://www.theregister.co.uk/2017/04/21/windows_hacked_nsa_shadow_brokers/
Jesus.
Security patches have to be tested by large organisations, they can't afford to just click 'update now' and hope for the best. That's assuming the infrastructure is up to date, it really wouldn't surprise me if server 2003 is still part of the NHS.
What a cluster F.
Of course 2003 is still in use. It is all over the place outside of the NHS too. I doubt it's anything to do with the cause of this.
The vulnerability is in Windows SMB server and a patch was issued mid-March.
AIUI the vulnerability was identified in March, it was patched in April. Not that it makes a vast amount if difference, but waiting a few weeks before patching in case of a broken patch is much less heinous than just lazy patching.
it really wouldn't surprise me if server 2003 is still part of the NHS.
It wouldn't surprise me if OS/2 Warp is still part of the NHS.
[quote=Cougar said]
It wouldn't surprise me if OS/2 Warp is still part of the NHS.
Great OS !
I work 1 evening a fortnight at NHS 111. Tonight is that night and it's mental here! A lot of services are falling back to us and it's just nuts busy. Never seen anything like it. Drafted in as many extra staff as could be found and it's buzzing but it's still mental.
It wouldn't surprise me if OS/2 Warp is still part of the NHS.
Great OS !
It's likely to be running on the cash machines the crooks will use to take their ill-gotten gains or from.... If they ever do.
Around 74 countries affected by this ransomware attack, apparently.
How much of the estate is still on XP and if so a choice was made to bin extended support on it, so MS wouldn't even have created a custom patch(es) for the Vuln(S) never mind getting round to deploying it.
https://www.theregister.co.uk/2015/05/26/uk_gov_bins_extended_windows_xp_support_contract/
I was sat in a session with Cisco today where we were looking at Stealthwatch along with Umbrella, Trustsec and ISE which would have seen the change in network traffic and you could have most likely spotted and isolated the affected machines pretty dammed quickly at a network level.
As we were playing with the Demo VM's of it all, one of the guys (different company to me) shouts out "my client (one of the authorities) has an worm outbreak and not to open any mail from them"
I'm in the process of looking at a network refresh of a large manufacturer and things like this will make my job a hell of a lot easier in recommending splitting the enterprise/production networks and putting some serious controls in place.
Not looking good for a lot of people.
[url= https://intel.malwaretech.com/WannaCrypt.html ]https://intel.malwaretech.com/WannaCrypt.html[/url]
Russell96 - MemberHow much of the estate is still on XP and if so a choice was made to bin extended support on it
Sadly Russ from what I have seen "quite a lot" is the answer 🙁
To give you an idea of how this sort of thing happens.-
At work we get a few spam, malicious , phishing scam emails. We have an in house IT guy who lets us know the latest threats and not to open them.
I opened our inbox and 2nd email was from an ex- employeee , he left about a year ago. In the subject line was " Invoice to Nic XXXXX "
Nic was standing next to me. I asked him if he had spoken to xyz in the last year , or had any dealings with him.
Nic answered in the negative so I knew it was hooky so without opening it I imediatly deleted the email .
The IT guy was in an other office so I popped down to tell him we were getting phished from XYZ's email address, and that I had deleted the email. ' Right thing to do , thanks for letting me know ' was his response.
Walk back to my PC , and Nic has gone into the deleted email folder and opened the email to see what it was as it had his name in the subject line .
'Its ok, it only infects your computer if you double click ' oh really Bill Gates. WTF went through your mind, having agreed with me it was sapm, trojan etc to go into the deleted folder and open the bloody thing.
I then had to go back to the IT guy ( still seething ) with my head in hands and say " You are not going to believe this but..."
IT bloke just been around. They've just had a patch through from NHS England which is being applied to my machine now. Seems like they're on top of it.
I then had to go back to the IT guy ( still seething ) with my head in hands and say " You are not going to believe this but..."
See, this is the issue. It's an arms race between techies building bigger and better idiot-proof systems, and nature building bigger and better idiots.
I got a Meraki security appliance a while back and never got round to fitting it, today has scared me enough that its getting installed on the home network tomorrow and there's going to be a fair bit of locking down on stuff.
Need to luck at what I can blag/get at a reasonable price for a decent DNS provider that provides some filtering on the malware, C2 etc type stuff.
I then had to go back to the IT guy ( still seething ) with my head in hands and say " You are not going to believe this but
Also (no offence but there's a certain irony here)
You walked away from your unlocked pc with a curious dorris stood next to it!!! 😀
even emergency surgery requires a computer at some stage
Will the NHS just have to pay up?
still could be worse...
From arstechnica: https://arstechnica.com/security/2017/05/an-nsa-derived-ransomware-worm-is-shutting-down-computers-worldwide/
It's apparently attacking Russia disproportionately...
However, the effect it's having on mission-critical systems worldwide is catastrophic.
It's apparently attacking Russia disproportionately...
could it be a bit of CIA revenge gone wrong?
Doesn't surprise me one bit, the NHS it utterly reliant on IT and largely refuses to invest money on it.
Well it's not as though the NHS has other priorities than IT to worry about ? 😯
could it be a bit of CIA revenge gone wrong?
Gotta say, it's timely on the back of the Conservative "ban irreversible encryption" notion.
Someone bought or rented an off the shelf ransomware package, modded it to take advantage of a recent vuln that has been patched on modern machines but that in itself gives you a massive clue that it hasn't on older OS's.
Fired it off almost on a scatter gun approach via email to various orgs, with say 800K-1M users in the NHS based on the email system with some of Matty's colleagues peers how many does it take?
The email system is across the NHS but each local HA has their own network, admin, IT etc so whilst the infection vector is common across the lot, the spread of it gives a good idea on where Matty's Colleagues Peers are and who's running un-patched or XP systems.
If only there was some sort of united group of like minded nations we were members of that were introducing a law to ensure security for critical gov infrastructre was supported
http://www.silicon.co.uk/data-storage/bigdata/gdpr-approved-european-parliament-190064